Cybersecurity shouldn't be a mystery. We demystify the threats and empower you with knowledge. Stay informed, stay protected.
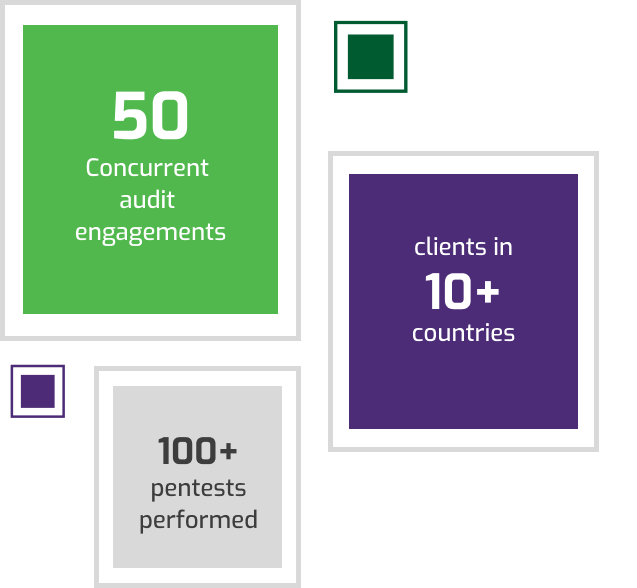
Our team will take stock of the existing IT Infrastructure using our exclusive procedures and assessment methodologies.
Our controls and governance frameworks are aligned to global best practices and compliances such as NIST, ISO 27001, GDPR, SOC1/SOC2 compliances etc.


We use licensed and cutting-edge tools and techniques to identify potential weaknesses in your network and web applications. Through penetration testing, we simulate real-world cyber-attacks to assess your organization's readiness and response to security breaches.